Cisco Smart Install - PORT 4786
Become VeryLazyTech member! 🎁
Follow us on:
✖ Twitter @VeryLazyTech.
👾 Github @VeryLazyTech.
📜 Medium @VeryLazyTech.
📺 YouTube @VeryLazyTech.
📩 Telegram @VeryLazyTech.
🕵️♂️ My Site @VeryLazyTech.
Visit our shop for e-books and courses. 📚
Basic info
Cisco Smart Install (SMI) is a plug-and-play feature designed to simplify deploying new Cisco devices:
Allows network admins to push configs and images automatically.
Runs on TCP port 4786.
Works without authentication (originally designed for trusted enterprise environments).
The problem? It trusted anyone connecting to it. 😎
Enumeration
Nmap:
To hunt on the entire internet (Shodan):
Exploitation
Several public PoCs exist. Let’s break it down:
Check if Smart Install is enabled:
In 2018, a critical vulnerability, CVE-2018–0171, was found in this protocol. The threat level is 9.8 on the CVSS scale.
A specially crafted packet sent to the TCP/4786 port, where Cisco Smart Install is active, triggers a buffer overflow, allowing an attacker to:
forcibly reboot the device
call RCE
steal configurations of network equipment.
The SIET (Smart Install Exploitation Tool) was developed to exploit this vulnerability, it allows you to abuse Cisco Smart Install. In this article I will show you how you can read a legitimate network hardware configuration file. Configure exfiltration can be valuable for a pentester because it will learn about the unique features of the network. And this will make life easier and allow finding new vectors for an attack.
The target device will be a “live” Cisco Catalyst 2960 switch. Virtual images do not have Cisco Smart Install, so you can only practice on the real hardware.
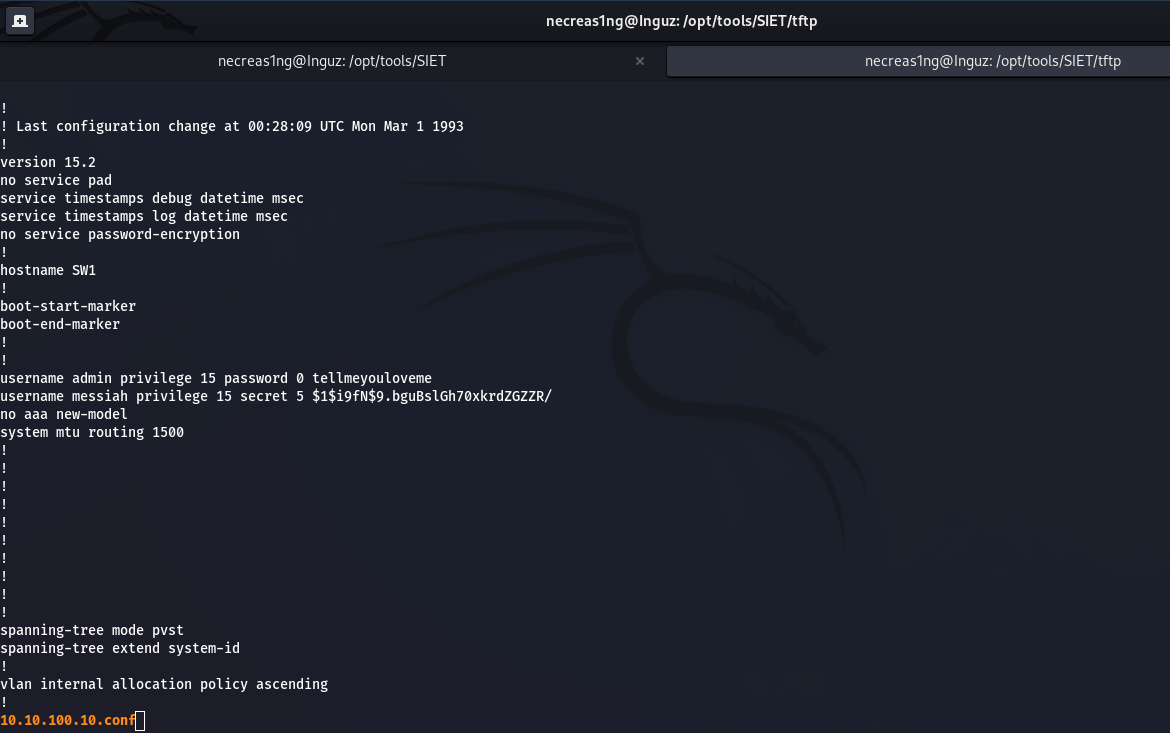
The address of the target switch is 10.10.100.10 and CSI is active. Load SIET and start the attack. The -g argument means exfiltration of the configuration from the device, the -i argument allows you to set the IP address of the vulnerable target.

The switch configuration 10.10.100.10 will be in the tftp/ folder
Vulnerability Breakdown (CVE-2018-0171)
Type: Remote Code Execution (RCE)
Affected Products: Cisco switches, routers, and Catalyst devices running Smart Install.
Attack Vector: Malicious Smart Install packets crafted to exploit buffer overflow.
Impact: Full device compromise (execute arbitrary code, wipe configs, reroute traffic).
POC: https://github.com/AlrikRr/Cisco-Smart-Exploit

Learn & practice For the Bug Bounty
Support VeryLazyTech 🎉
Become VeryLazyTech member! 🎁
Follow us on:
✖ Twitter @VeryLazyTech.
👾 Github @VeryLazyTech.
📜 Medium @VeryLazyTech.
📺 YouTube @VeryLazyTech.
📩 Telegram @VeryLazyTech.
🕵️♂️ My Site @VeryLazyTech.
Visit our shop for e-books and courses. 📚
Last updated