Subdomain Takeover
Become VeryLazyTech member! 🎁
Follow us on:
✖ Twitter @VeryLazyTech.
👾 Github @VeryLazyTech.
📜 Medium @VeryLazyTech.
📺 YouTube @VeryLazyTech.
📩 Telegram @VeryLazyTech.
🕵️♂️ My Site @VeryLazyTech.
Visit our shop for e-books and courses. 📚
Subdomain takeovers are a critical vulnerability that allows attackers to seize control of a subdomain by exploiting misconfigurations in DNS settings. These attacks can lead to phishing, data leaks, and malicious redirection, and they are highly valuable for both penetration testers and bug bounty hunters. This guide will walk you through every step of identifying and exploiting subdomain takeovers using practical techniques, diverse tools, and real-world examples.
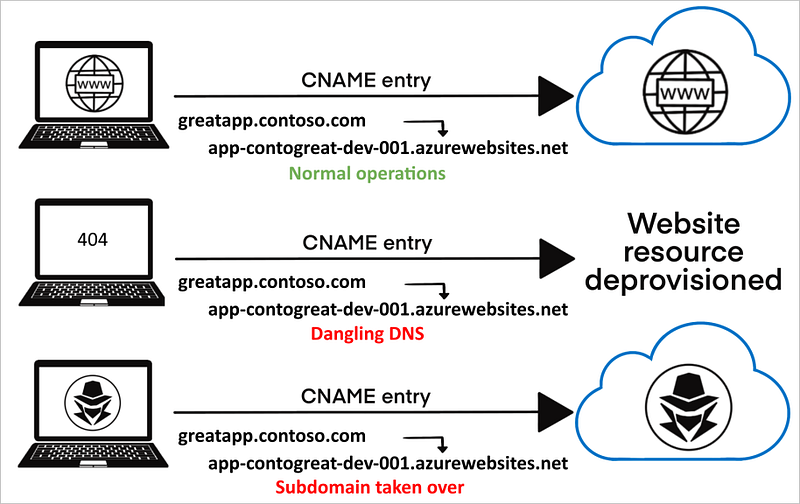
What is Subdomain Takeover?
Subdomain takeover happens when a subdomain points to an external service (like GitHub Pages, AWS S3, Heroku, etc.), but the service is not properly configured. The DNS record remains in place, but the resource it points to is no longer active or owned, leaving the subdomain vulnerable to exploitation.
Why is it Dangerous?
Phishing Attacks: Attackers can impersonate the domain to trick users into providing sensitive information.
Defacement: Attackers can host malicious content on the subdomain, impacting the organization’s reputation.
Hijacking Subdomain Trust: Since the subdomain is part of a trusted domain, it may bypass security filters or add credibility to attacks.
Step-by-Step Guide to Subdomain Takeover
Enumerating Subdomains
The first step in exploiting subdomain takeovers is identifying which subdomains are in use by the target. Subdomain enumeration helps you discover a list of subdomains that may be vulnerable.
Tools and Commands:
Subfinder:
Subfinder is an excellent tool for passive subdomain enumeration that pulls data from public sources.
Amass:
Amass performs both passive and active enumeration, giving a comprehensive list of subdomains.
Subfinder and Amass are useful for quickly gathering subdomains that may be pointing to third-party services. These tools provide a good starting point for vulnerability assessment.
Identifying Vulnerable Subdomains
Once you’ve collected subdomains, the next step is checking whether any subdomains are vulnerable to takeover. The subdomains that are candidates for takeover often point to cloud services like AWS, GitHub Pages, or Heroku, where the resource has been deleted or not claimed.
Tools and Commands:
HTTP Probing (httprobe):
This will filter out only the subdomains that are alive by checking if they return a valid HTTP response.
Check for CNAME Records (dig):
CNAME records can help identify if a subdomain points to a third-party service like GitHub, AWS, or Heroku.
If you see that a CNAME record exists for a service like github.io, but the resource doesn’t return any valid content (e.g., a 404 or default error message), the subdomain could be vulnerable.
Exploiting the Vulnerability
Once a vulnerable subdomain is identified, the next step is claiming the resource and exploiting the takeover.
Common Services Prone to Subdomain Takeover:
GitHub Pages: If a subdomain is pointing to GitHub Pages (username.github.io) but no repository exists, you can create a repository and claim the subdomain.
AWS S3 Buckets: If a subdomain points to an S3 bucket (bucket-name.s3.amazonaws.com) but the bucket is unclaimed, you can create a bucket with the same name.
Heroku: If a subdomain points to Heroku (herokuapp.com) and the app is deleted, you can create an app with the same name.
The process of taking over these services involves reclaiming the abandoned resources and linking them to your content, effectively gaining control over the subdomain.
Automating the Detection (Subjack and Nuclei)
To streamline the process of finding and exploiting subdomain takeovers, automation tools like Subjack and Nuclei are highly effective.
Subjack automates the detection of vulnerable subdomains by checking for misconfigurations in popular cloud services.
Nuclei is a vulnerability scanning tool that can be used with specific templates for subdomain takeovers.
Using these tools speeds up the process by automatically identifying potential takeovers without the need for manual probing. This allows for larger-scale testing, especially useful in bug bounty programs.
Common Services Vulnerable to Subdomain Takeover
GitHub Pages (
username.github.io)AWS S3 (
bucket-name.s3.amazonaws.com)Heroku (
herokuapp.com)Shopify (
shops.myshopify.com)Azure Blob Storage (
accountname.blob.core.windows.net)
Each of these services, when misconfigured or abandoned, leaves a subdomain exposed to takeover. By knowing how to check for specific services, you can more efficiently discover and exploit these vulnerabilities.
Last updated