LDAP - Ports 389, 636, 3268, 3269
Become VeryLazyTech member! 🎁
Follow us on:
✖ Twitter @VeryLazyTech.
👾 Github @VeryLazyTech.
📜 Medium @VeryLazyTech.
📺 YouTube @VeryLazyTech.
📩 Telegram @VeryLazyTech.
🕵️♂️ My Site @VeryLazyTech.
Visit our shop for e-books and courses. 📚
Basic Info
LDAP (Lightweight Directory Access Protocol) is a protocol used for accessing and managing directory information services. It is commonly used in Windows Active Directory and Linux directory services.
Ports:
TCP 389 (unencrypted LDAP)
TCP 636 (LDAPS - LDAP over SSL/TLS)
TCP 3268 (Global Catalog for domain-wide searches)
TCP 3269 (Secure Global Catalog)
Authentication Types:
Anonymous bind
Simple authentication (username/password)
SASL authentication (Kerberos, NTLM, Digest-MD5)
LDAP Data Interchange Format
LDIF (LDAP Data Interchange Format) defines the directory content as a set of records. It can also represent update requests (Add, Modify, Delete, Rename).
Lines 1-3 define the top level domain local
Lines 5-8 define the first level domain moneycorp (moneycorp.local)
Lines 10-16 define 2 organizational units: dev and sales
Lines 18-26 create an object of the domain and assign attributes with values
Write data
Note that if you can modify values you could be able to perform really interesting actions. For example, imagine that you can change the "sshPublicKey" information of your user or any user. It's highly probable that if this attribute exist, then ssh is reading the public keys from LDAP. If you can modify the public key of a user you will be able to login as that user even if password authentication is not enabled in ssh.
Anonymous Access
Bypass TLS SNI check
According to this writeup just by accessing the LDAP server with an arbitrary domain name (like company.com) he was able to contact the LDAP service and extract information as an anonymous user:
LDAP anonymous binds
LDAP anonymous binds allow unauthenticated attackers to retrieve information from the domain, such as a complete listing of users, groups, computers, user account attributes, and the domain password policy. This is a legacy configuration, and as of Windows Server 2003, only authenticated users are permitted to initiate LDAP requests. However, admins may have needed to set up a particular application to allow anonymous binds and given out more than the intended amount of access, thereby giving unauthenticated users access to all objects in AD.
Valid Credentials
If you have valid credentials to login into the LDAP server, you can dump all the information about the Domain Admin using:
Enumerating LDAP Services
Before attacking LDAP, we must enumerate the target environment.
2.1 Scanning for LDAP Services
Use nmap to discover LDAP services:
2.2 LDAP Enumeration with windapsearch orldapsearch
ldapsearchwindapsearch
Windapsearch is a Python script useful to enumerate users, groups, and computers from a Windows domain by utilizing LDAP queries.
Check null credentials or if your credentials are valid:
If you find something saying that the "bind must be completed" means that the credentials are incorrect.
You can extract everything from a domain using:
Extract users:
Extract computers:
Extract my info:
Extract Domain Admins:
Extract Domain Users:
Extract Enterprise Admins:
Extract Administrators:
Extract Remote Desktop Group:
To see if you have access to any password you can use grep after executing one of the queries:
Please, notice that the passwords that you can find here could not be the real ones...
pbis
You can download pbis from here: https://github.com/BeyondTrust/pbis-open/ and it's usually installed in /opt/pbis.
Pbis allow you to get basic information easily:
Graphical Interface
Apache Directory
Download Apache Directory from here. You can find an example of how to use this tool here.
jxplorer
You can download a graphical interface with LDAP server here: http://www.jxplorer.org/downloads/users.html
By default is is installed in: /opt/jxplorer
Godap
Godap is an interactive terminal user interface for LDAP that can be used to interact with objects and attributes in AD and other LDAP servers. It is available for Windows, Linux and MacOS and supports simple binds, pass-the-hash, pass-the-ticket & pass-the-cert, along with several other specialized features such as searching/creating/changing/deleting objects, adding/removing users from groups, changing passwords, editing object permissions (DACLs), modifying Active-Directory Integrated DNS (ADIDNS), exporting to JSON files, etc.
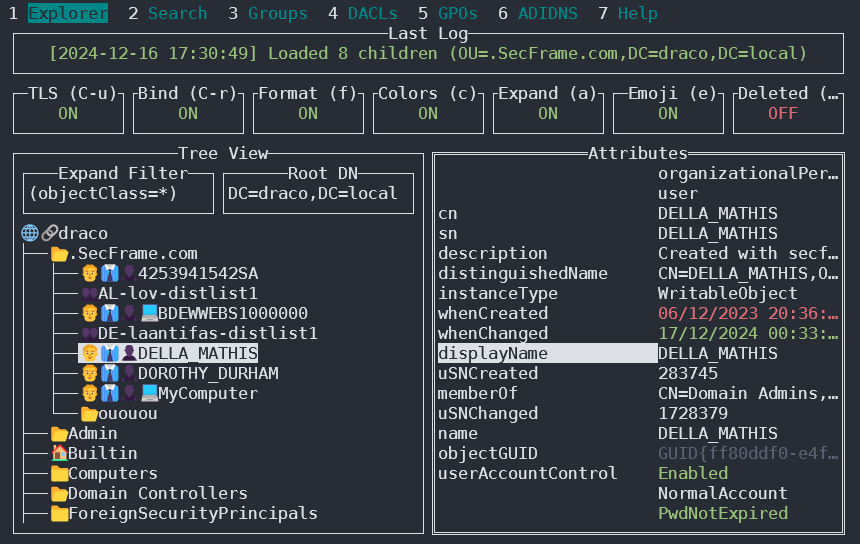
You can access it in https://github.com/Macmod/godap. For usage examples and instructions read the Wiki.
Ldapx
Ldapx is a flexible LDAP proxy that can be used to inspect & transform LDAP traffic from other tools. It can be used to obfuscate LDAP traffic to attempt to bypass identity protection & LDAP monitoring tools and implements most of the methods presented in the MaLDAPtive talk.
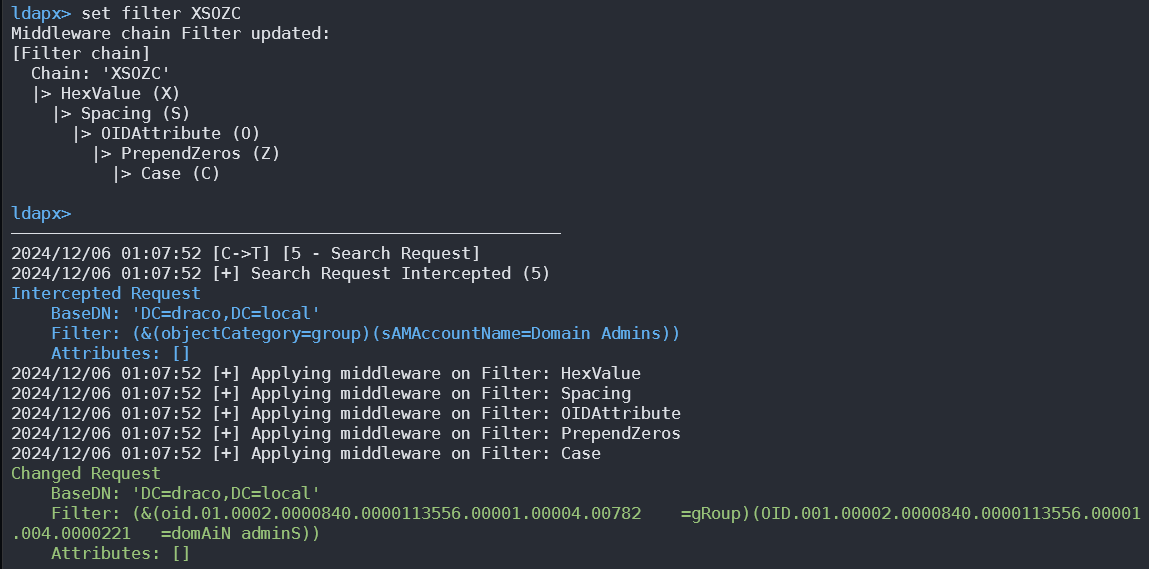
You can get it from https://github.com/Macmod/ldapx.
Exploiting Anonymous Binds
If anonymous binds are enabled, we can extract:
Users
Groups
Policies
Check anonymous access:
If successful, dump the entire directory:
Attacking LDAP Authentication
4.1 Valid Credential Enumeration
If we have a valid username and password:
4.2 Brute Force Attack
Using nmap:
Using medusa:
Modifying LDAP Attributes (Privilege Escalation)
If we have write permissions, we can inject an SSH key or modify user permissions:
Sniffing LDAP Traffic
If LDAP is not using encryption, credentials can be intercepted using Wireshark:
Filter:
ldap && ip.addr==<target-IP>Look for bindRequest packets containing usernames and passwords.
Configuration Files
General
containers.ldif
ldap.cfg
ldap.conf
ldap.xml
ldap-config.xml
ldap-realm.xml
slapd.conf
IBM SecureWay V3 server
V3.sas.oc
Microsoft Active Directory server
msadClassesAttrs.ldif
Netscape Directory Server 4
nsslapd.sas_at.conf
nsslapd.sas_oc.conf
OpenLDAP directory server
slapd.sas_at.conf
slapd.sas_oc.conf
Sun ONE Directory Server 5.1
75sas.ldif
Learn & practice For the OSCP.
Support VeryLazyTech 🎉
Become VeryLazyTech member! 🎁
Follow us on:
✖ Twitter @VeryLazyTech.
👾 Github @VeryLazyTech.
📜 Medium @VeryLazyTech.
📺 YouTube @VeryLazyTech.
📩 Telegram @VeryLazyTech.
🕵️♂️ My Site @VeryLazyTech.
Visit our shop for e-books and courses. 📚
Last updated