Identify a Server’s Origin IP
Become VeryLazyTech member! 🎁
Follow us on:
✖ Twitter @VeryLazyTech.
👾 Github @VeryLazyTech.
📜 Medium @VeryLazyTech.
📺 YouTube @VeryLazyTech.
📩 Telegram @VeryLazyTech.
🕵️♂️ My Site @VeryLazyTech.
Visit our shop for e-books and courses. 📚
What is an Origin IP?
An Origin IP refers to the actual IP address of a server hosting a website or application. Many websites today use Content Delivery Networks (CDNs) like Cloudflare, Akamai, and Amazon CloudFront to mask their true IP addresses for security, performance, and reliability reasons. These CDNs act as reverse proxies, handling all incoming traffic and providing:
DDoS Protection: Absorbs and mitigates malicious traffic to prevent downtime.
Load Balancing: Distributes traffic to multiple servers to ensure availability.
Content Caching: Stores static content closer to users to improve performance (such as images, CSS, and JavaScript files).
When you make an HTTP request to a domain using a CDN, you are actually communicating with the CDN’s edge servers rather than the real server. This prevents attackers from easily discovering the actual server hosting the website.
Why is Identifying an Origin IP Important?
Finding the real server IP address is critical for cybersecurity researchers, penetration testers, and even malicious attackers. It allows them to:
Map network infrastructure and locate services operating on different IPs.
Bypass CDN protection to test for vulnerabilities directly.
Launch targeted attacks such as DDoS, direct exploitation, and reconnaissance.
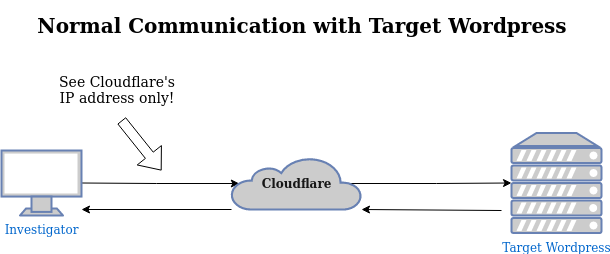
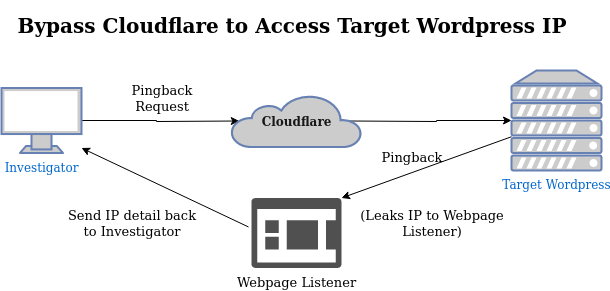
Compare with this next diagram, showing how a pingback will convince the Wordpress server to reach out to our “honeypot” pingback server which relays the IP address it finds back to us.
How to Find the Origin IP of a Server
Despite the protection offered by CDNs, several techniques can help reveal a server’s real IP address. Below are some of the most effective methods.
1. Using WHOIS and Host Lookup
First, we can use whois and host to gather more information about the target domain:
These results confirm that the domain is behind Cloudflare, meaning requests are routed through the CDN.
2. SSL Certificates Enumeration
SSL certificates can reveal the origin server’s IP by analyzing its public certificate information. Tools like Censys and crt.sh can help.
Visit https://search.censys.io/ and enter the target domain.
Look for associated IP addresses.
Use
curlto verify:
Response:
This method is one of the simplest and most efficient ways to identify the real IP address of a target. Keep in mind that the different IP addresses identified during our investigation won’t necessarily be the host IPs for enji.ai, but they provide valuable clues about the present subnet and expanding our attack surface.
3. Subdomain Enumeration
Subdomains often bypass the CDN, exposing real IP addresses. Use Subfinder to find them:
Next, verify whether the subdomain is routed through the CDN:
If the IP is different from the main domain, it might be the origin server.
4. Analyzing DNS Records
By examining the DNS records of a domain, an attacker could potentially discover previously exposed IP addresses of the server from times when it was not behind a CDN. DNS records provide various types of information about a domain, and by analyzing these records, penetration testers can gather valuable insights that may lead to the discovery of the origin IP.
Types of DNS records
Different types of DNS records can reveal specific details about the domain and its infrastructure:
A Records: These records map a domain name to an IPv4 address. By examining historical A records, one can find previous IP addresses that may have been used by the domain before switching to a CDN.
AAAA Records: Similar to A records but for IPv6 addresses. Historical AAAA records can also provide information on previous IPv6 addresses.
MX Records: Mail Exchange records specify the mail servers responsible for receiving email on behalf of the domain. Sometimes, these mail servers are not routed through the CDN, revealing the real IP address.
TXT Records: Text records can contain various forms of information, including verification details for email services and other metadata. Occasionally, these records might inadvertently expose internal IP addresses or other sensitive information.
CNAME Records: Canonical Name records alias one domain to another. By following the chain of CNAME records, it’s possible to uncover the origin domain that might point directly to the real server IP.
Checking past DNS records can uncover previously exposed IP addresses. Use dig:
For subdomains:
Here, we discovered AWS Elastic Load Balancer (ELB) IPs, likely exposing the origin server.
5. Checking CDN IP Ranges
If a website uses AWS, Google Cloud, or another provider, you can search its CDN IP ranges. Use grep to match:
This method helps uncover IPs that might not be fully hidden behind the CDN.
6. Host Header Fuzzing
Fuzzing with custom Host headers can sometimes bypass CDNs:
If the response differs from a CDN-protected response, it’s likely the real server.
7. WordPress Pingback Exploit
For WordPress sites, use XML-RPC pingbacks to reveal the origin IP:
If the response contains an IP address, it’s the origin server.
8. Using CloudFlair Tool
CloudFlair automates CDN bypassing by scanning for related IPs:
We can send a GET request to one of the found IP's and get this:
This tool utilizes Censys API to find origin IP addresses related to a domain.
Conclusion
Identifying a server’s real IP address can be crucial for penetration testing, cybersecurity research, and ethical hacking. While CDNs like Cloudflare offer strong protection, there are multiple techniques — such as SSL analysis, DNS lookups, subdomain enumeration, and CDN range checking — that can help bypass them.
Learn & practice For the OSCP.
Support VeryLazyTech 🎉
Become VeryLazyTech member! 🎁
Follow us on:
✖ Twitter @VeryLazyTech.
👾 Github @VeryLazyTech.
📜 Medium @VeryLazyTech.
📺 YouTube @VeryLazyTech.
📩 Telegram @VeryLazyTech.
🕵️♂️ My Site @VeryLazyTech.
Visit our shop for e-books and courses. 📚
Last updated