CMS Wp/Durpal/Joomla/etc..
Become VeryLazyTech member! 🎁
Follow us on:
✖ Twitter @VeryLazyTech.
👾 Github @VeryLazyTech.
📜 Medium @VeryLazyTech.
📺 YouTube @VeryLazyTech.
📩 Telegram @VeryLazyTech.
🕵️♂️ My Site @VeryLazyTech.
Visit our shop for e-books and courses. 📚
WordPress
Basic Info
WordPress File & Path Basics
Uploads →
/wp-content/uploads/YYYY/MM/filenameExample:http://10.10.10.10/wp-content/uploads/2018/08/a.txtThemes →
/wp-content/themes/[theme]/Uploading a malicious file or editing PHP templates may provide RCE.
Example:
/wp-content/themes/twentytwelve/404.php
Default login paths →
/wp-login.php /wp-login/ /wp-admin/ /wp-admin.php /login/Important files:
wp-config.php→ Database credentials, salts, debug settings.license.txt→ May reveal WordPress version.xmlrpc.php→ Remote procedure call interface (often abused).wp-sitemap.xml→ Introduced in WP 5.5, lists public posts & taxonomies.wp-includes/→ Core libraries (JS, fonts, widgets, certs).wp-content/→ Plugins & themes directory.
Post exploitation
The
wp-config.phpfile contains information required by WordPress to connect to the database such as the database name, database host, username and password, authentication keys and salts, and the database table prefix. This configuration file can also be used to activate DEBUG mode, which can useful in troubleshooting.
WordPress User Roles
Administrator → Full control over site.
Editor → Manage own + others’ posts.
Author → Manage and publish own posts.
Contributor → Write posts, but cannot publish.
Subscriber → Read posts & manage their profile.
Wordpress - Enumeration
Passive Enumeration
Passive techniques rely on publicly accessible resources without direct interaction that might raise alarms.
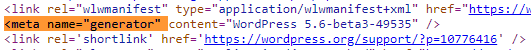
1. Identify WordPress Version
license.txtorreadme.htmlmay disclose version.HTML meta tags:
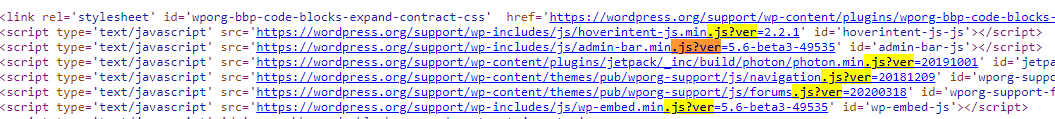
Inspect linked CSS/JS files (
?ver=X.Y.Z).
2. Enumerate Plugins & Themes
Plugins:
Themes:
3. Extract Versions from Assets
Active enumeration
Plugins and Themes
You probably won't be able to find all the Plugins and Themes passible. In order to discover all of them, you will need to actively Brute Force a list of Plugins and Themes (hopefully for us there are automated tools that contains this lists).
1. User Enumeration
Author ID brute-force:
200/30X= valid ID400= invalid ID
WP REST API:
Login error messages → Differentiate valid vs. invalid usernames.
2. User Information via JSON
Posts API:
Pages API (may leak IPs):
3. XML-RPC Abuse
Check availability:

Credential brute-force methods (bruteforce by https://github.com/relarizky/wpxploit):
wp.getUsersBlogs
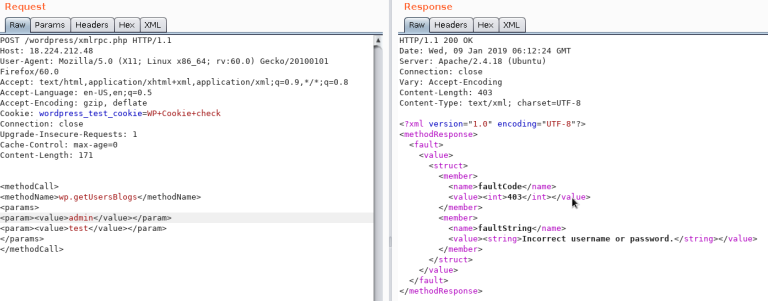
wp.getCategoriesmetaWeblog.getUsersBlogs
File upload example with
wp.uploadFile: (useful for shell upload if creds valid).Optimization → Use
system.multicallfor faster brute force attempts.
Using the correct credentials you can upload a file. In the response the path will appears
Also there is a faster way to brute-force credentials using system.multicall as you can try several credentials on the same request:

Automatic Tools
CMSmap
CMSmap is a python tool to automate the process of detecting and exploiting vulnerabilities in CMSs (WordPress, Joomla, Drupal, etc.)
-s : target site
-t : number of threads
-a : custom User-Agent
WPScan
WPScan is specialized for WordPress vulnerability scanning.
--rua : use a random User-Agent
-e : enumerate users, plugins, themes, timthumbs, config backups, DB exports, media
--url : target WordPress site
--plugins-detection : plugin detection mode (aggressive, mixed, passive)
--api-token : WPScan API token (free plan allows ~50 requests/day)
Learn & practice For the Bug Bounty
Support VeryLazyTech 🎉
Become VeryLazyTech member! 🎁
Follow us on:
✖ Twitter @VeryLazyTech.
👾 Github @VeryLazyTech.
📜 Medium @VeryLazyTech.
📺 YouTube @VeryLazyTech.
📩 Telegram @VeryLazyTech.
🕵️♂️ My Site @VeryLazyTech.
Visit our shop for e-books and courses. 📚
Last updated